 (NewsUSA)
(NewsUSA) – As the holiday season approaches, so does the dilemma of holiday and year-end gift-giving. Whether you are seeking something for a friend, family member, or long-absent colleague, edible gifts are a can’t-miss choice, and the range of tasty treats goes far beyond a prepacked gift basket.
– As the holiday season approaches, so does the dilemma of holiday and year-end gift-giving. Whether you are seeking something for a friend, family member, or long-absent colleague, edible gifts are a can’t-miss choice, and the range of tasty treats goes far beyond a prepacked gift basket.
Like many big ideas, Hahn’s Old Fashioned Cake Company started small.
“All our cakes are baked fresh daily, and feature extra-large handmade crumbs,” says owner Andrew Hahn, whose mother and father started Hahn’s Old-Fashioned Cake Company in her kitchen.
The current selection of crumb cakes was inspired by an old family recipe that Mr. and Mrs. Hahn often made for friends and neighbors.
Word got out, and an expanding circle of crumb-cake fans began requesting cakes. A business was born, and it has been family-owned and operated for more than 35 years.
Key features that set Hahn’s crumb cakes apart include:
– Quality. Hahn’s crumb cakes are made fresh daily, with fresh eggs to create a moist base with optimum texture. They are popular not only as individual sales, but sell well in delis, coffee shops, and gourmet food markets.
– Convenience. Hahn’s cakes are packed to ship or enjoy right away. For those lucky enough to live locally, curbside pickup and delivery are available in a limited radius through DoorDash and GrubHub.
– Crumbs. Crumbs and more crumbs. For those who can’t resist picking the crumbs off a crumb cake, Hahn’s has you covered.
The company recognizes the crumb-obsessed, and fills that niche with a Can of Crumbs or a Bucket of Crumbs. These ready-to-eat crumb treats are considered by many to be the best part of a crumb cake, and the bucket lends itself to easy shipping and gift-giving as well.
Crumb cake flavors include the original plain crumb cake (with plenty of crumbs), raspberry walnut, apple, and chocolate. There’s something for brownie lovers, too; the company bakes a classic, fudgy chocolate brownie of the same caliber as its cakes.
Hahn’s Old-Fashioned Cakes also offers fundraising opportunities for schools, churches, and non-profit organizations.
Visit crumbcake.com for more information.
Massive Volunteer Effort Touches 18 States
 (NewsUSA)
(NewsUSA) – Williams is an energy infrastructure company that is fueling the clean energy economy. This spring, hundreds of Williams employees gave their own energy to complete more than 160 community projects across 18 states during the company’s inaugural volunteer week.
– Williams is an energy infrastructure company that is fueling the clean energy economy. This spring, hundreds of Williams employees gave their own energy to complete more than 160 community projects across 18 states during the company’s inaugural volunteer week.
“Strong community involvement is at the heart of Williams, driven by our core value to be responsible stewards,” says Alan Armstrong, president and chief executive officer of Williams, which handles 30 percent of the nation’s natural gas. “By harnessing the energy and enthusiasm of our employees, we’re exemplifying our values by lending a hand to the nonprofits that work hard every day to improve our communities.”
Williams volunteer week builds on the company’s long tradition of being a good neighbor through employee volunteerism and financial support. Projects this year ranged from outdoor beautification to volunteering in elementary school classrooms to helping at food banks.
In Houston, employees revitalized a community garden in an underserved area. Williams employee Jerry Fabian is on the board of directors for nonprofit Urban Harvest, which has a mission to increase access to fresh and local food. The Happy Place Garden serves a low-income population.
“This area is classified as a food desert, meaning many residents live away from a supermarket or grocery store with healthy food options. The goal is to revitalize this garden so that the neighborhood can once again plant and harvest nutritious foods from the allotted beds, plus also have a safe space for the neighbors to gather and build social cohesion.”
Fabian, a supervisor of project controls at Williams, says employee volunteerism is not just a duty, but a privilege.
“While we are supporting the areas where we work, live and play, we are also helping to create a sustainable and safe community for everyone. Obviously, volunteering has a positive impact on the communities, but it also creates a positive and lasting feeling of achievement.”
In North Carolina, Williams’ Coordinator of Maintenance Chad Dlugoszewski says it feels good to help a local nonprofit needing volunteers with skills in repairs and construction. At the Ada Jenkins Center in Davidson, N.C., employees repaired roofs, sanded and painted walls, assembled pantry shelving and pruned trees.
“The center rarely has volunteers with the skills required for upkeep and repairs to their 85-year-old building,” Dlugoszewski says. “Partnering with Williams for the volunteer project allowed them to make repairs that have been needed for years.”
In western Georgia, employees documented thousands of gravestones at a nearby cemetery. The project, in coordination with Billion Graves, will add to an online database of gravestones that can then be located by longitude and latitude, says Tina Kitchens, a senior field office administrator at Williams.
“There is a huge need to record all gravestones so that relatives and descendants can search for their loved ones,” says Kitchens. “Some of the gravestones date back decades and are too dirty to read, so we will carefully and respectfully wash them and load the images to the Billion Graves app.”
Kitchens says Williams’ support of volunteer efforts is meaningful to both employees and those in need.
“It makes us feel good to do something for others,” she says. “I hope if I was in need, there would be caring people out there to help.”
These are just a few of the many volunteer projects completed across the nation by Williams employees in only one week. To learn more about Williams and see photos from its volunteer week, visit Williams.com.
Strategies for a Smooth Retirement on a Fixed Income
 (NewsUSA)
(NewsUSA) – When making financial plans for retirement on a fixed income, remember that your retirement life at the beginning is not how it will continue indefinitely. A CERTIFIED FINANCIAL PLANNERTM professional will assist you in creating a smooth retirement plan that best fits your needs over time. “Your retirement will evolve in phases as your priorities change,” says Cary Carbonaro, CFP.® “One of the most important things you can do right now is understand how your retirement will change and then budget for those different phases.”Carbonaro suggests thinking of retirement in three phases:
– When making financial plans for retirement on a fixed income, remember that your retirement life at the beginning is not how it will continue indefinitely. A CERTIFIED FINANCIAL PLANNERTM professional will assist you in creating a smooth retirement plan that best fits your needs over time. “Your retirement will evolve in phases as your priorities change,” says Cary Carbonaro, CFP.® “One of the most important things you can do right now is understand how your retirement will change and then budget for those different phases.”Carbonaro suggests thinking of retirement in three phases:
- Early: The early years of retirement are the years when most retirees enjoy good health and are free of work and child-rearing, allowing travel and other activities to play a larger role in the budget.
- Middle: This phase can be considered a slowing-down and transitional phase for many. Changes in health, legacy and other goals will impact financial plans and budgeting.
- Late: Late retirement is when healthcare and other similar issues take priority.
Regardless of your phase of retirement, it’s important to consider all your sources of retirement income. For most people, these include savings, investments and Social Security. Some people also have a pension plan from a former employer.Keys to successful financial planning on a fixed income include:
- Organizing withdrawals. You can choose to withdraw from retirement accounts monthly, but other options are annual, semi- annual or quarterly. Set up a plan that meets your needs.
- Budgeting. Your fixed-income budget will likely evolve, but it is important to have a plan in place so you can balance money for fun and adventure with a cushion for unexpected retirement expenses that could drain your savings.
- Considering costs. One often-overlooked expense when planning a retirement budget is the taxes on retirement account withdrawals. Carbonaro recommends withholding at least 20% to 25% of a withdrawal for taxes.
When developing a financial plan, retirees on a fixed income should also factor in the need for long-term care, which might involve paying for personal assistance with bathing, dressing and taking medications.Caring for adult children also is becoming a more common source of costs for retirees. Census data suggest that more than one-third of adults aged 18 to 34 are living in their parents’ home. In some cases, the situation is reversed, and retirees find themselves moving in with their adult children, either as a matter of preference or because of the expense of long-term care.For more information on financial planning strategies on a fixed income, visit LetsMakeAPlan.org.
Turning 65: What to Consider When Selecting a Medicare Plan
 (NewsUSA)
(NewsUSA) – Approaching age 65 can be an overwhelming time for many newly eligible Medicare beneficiaries. When can you begin to enroll? Which plans should you consider? What do you need to know?Here’s some information that can help.You have a seven-month window called the Initial Enrollment Period (IEP) to sign up for Medicare benefits, which begins three months prior to the month you’ll turn 65. You are first eligible to receive Medicare coverage at the start of your birthday month. If your current benefits end once you turn 65, it’s important to begin researching and comparing your Medicare options early to make sure there’s no gap in your coverage.There are several different types of Medicare plans available:* Medicare Part A (hospital) and Medicare Part B (medical)o Administered by the federal government, Original Medicare includes Parts A and B that provide hospital and medical coverage. For most people, Part A is free, so it’s important to evaluate your options as soon as you become eligible for Medicare.* Medicare Part C (Medicare Advantage)o Offered by Medicare-approved private insurance companies and can be considered an “all in one” alternative to Original Medicare. These plans include all the coverage provided by Medicare Part A and B, and some may include additional benefits like prescription drug coverage, routine dental, vision and hearing care, and innovative offerings such fitness programs, healthy food debit cards for those who qualify and transportation benefits to help you get to doctor’s appointments.* Medicare Part D (Prescription Drug Plans)o Original Medicare doesn’t cover most prescription drugs, so you’ll need to sign-up for a stand-alone prescription drug plan (PDP) if enrolled in Original Medicare. These Part D plans are offered by Medicare-approved private insurers, like Humana.* Medicare Supplement Insurance (Medigap)o Like Medicare Advantage, these plans are offered by private insurance companies and may help pay some of the healthcare costs that Medicare Parts A and B don’t, like coinsurance, copayments or deductibles.When selecting a prescription drug plan, you’ll want to make sure the medications you’re currently taking are covered and compare their costs across different plans. Some plans also take steps to help save you money, like Humana for example. They suggest generic or lower-cost equivalent drugs to their members when they’re available. And when it comes to costs, look beyond the monthly premium and consider the additional out-of-pocket costs. Always evaluate the full cost of the plan, including co-payments or co-insurance, and the deductible as well as which pharmacies are in network.While the many plan options can seem overwhelming, there are resources available to help you choose Medicare coverage that best suits your needs. The Medicare Plan Finder on Medicare.gov allows you to easily compare the benefits and costs of different plans. Other resources on sites such as Humana.com include helpful information to consider in shopping for plans like Physician and Pharmacy finders to help you see if your providers are in a plan’s network. While planning ahead is helpful, rest assured that, as your needs change, you can change your plan during the Medicare Advantage and Prescription Drug Plan Annual Enrollment Period, which goes from October 15th to December 7th each year.Medicare-eligible individuals can visit www.Medicare.gov or call 1-800-MEDICARE (800-633-4227), 24 hours a day, seven days a week. Additionally, you can learn about Humana Medicare Advantage and Prescription Drug Plans by going to www.Humana.com/Medicare, www.Humana.com/pdp or calling 1-800-213-5286 (TTY: 711) to speak with a licensed sales agent from 8 a.m. to 8 p.m. local time, seven days a week. Humana is a Medicare Advantage HMO, PPO, PDP, and PFFS organization with a Medicare contract. Enrollment in any Humana plan depends on contract renewal.
– Approaching age 65 can be an overwhelming time for many newly eligible Medicare beneficiaries. When can you begin to enroll? Which plans should you consider? What do you need to know?Here’s some information that can help.You have a seven-month window called the Initial Enrollment Period (IEP) to sign up for Medicare benefits, which begins three months prior to the month you’ll turn 65. You are first eligible to receive Medicare coverage at the start of your birthday month. If your current benefits end once you turn 65, it’s important to begin researching and comparing your Medicare options early to make sure there’s no gap in your coverage.There are several different types of Medicare plans available:* Medicare Part A (hospital) and Medicare Part B (medical)o Administered by the federal government, Original Medicare includes Parts A and B that provide hospital and medical coverage. For most people, Part A is free, so it’s important to evaluate your options as soon as you become eligible for Medicare.* Medicare Part C (Medicare Advantage)o Offered by Medicare-approved private insurance companies and can be considered an “all in one” alternative to Original Medicare. These plans include all the coverage provided by Medicare Part A and B, and some may include additional benefits like prescription drug coverage, routine dental, vision and hearing care, and innovative offerings such fitness programs, healthy food debit cards for those who qualify and transportation benefits to help you get to doctor’s appointments.* Medicare Part D (Prescription Drug Plans)o Original Medicare doesn’t cover most prescription drugs, so you’ll need to sign-up for a stand-alone prescription drug plan (PDP) if enrolled in Original Medicare. These Part D plans are offered by Medicare-approved private insurers, like Humana.* Medicare Supplement Insurance (Medigap)o Like Medicare Advantage, these plans are offered by private insurance companies and may help pay some of the healthcare costs that Medicare Parts A and B don’t, like coinsurance, copayments or deductibles.When selecting a prescription drug plan, you’ll want to make sure the medications you’re currently taking are covered and compare their costs across different plans. Some plans also take steps to help save you money, like Humana for example. They suggest generic or lower-cost equivalent drugs to their members when they’re available. And when it comes to costs, look beyond the monthly premium and consider the additional out-of-pocket costs. Always evaluate the full cost of the plan, including co-payments or co-insurance, and the deductible as well as which pharmacies are in network.While the many plan options can seem overwhelming, there are resources available to help you choose Medicare coverage that best suits your needs. The Medicare Plan Finder on Medicare.gov allows you to easily compare the benefits and costs of different plans. Other resources on sites such as Humana.com include helpful information to consider in shopping for plans like Physician and Pharmacy finders to help you see if your providers are in a plan’s network. While planning ahead is helpful, rest assured that, as your needs change, you can change your plan during the Medicare Advantage and Prescription Drug Plan Annual Enrollment Period, which goes from October 15th to December 7th each year.Medicare-eligible individuals can visit www.Medicare.gov or call 1-800-MEDICARE (800-633-4227), 24 hours a day, seven days a week. Additionally, you can learn about Humana Medicare Advantage and Prescription Drug Plans by going to www.Humana.com/Medicare, www.Humana.com/pdp or calling 1-800-213-5286 (TTY: 711) to speak with a licensed sales agent from 8 a.m. to 8 p.m. local time, seven days a week. Humana is a Medicare Advantage HMO, PPO, PDP, and PFFS organization with a Medicare contract. Enrollment in any Humana plan depends on contract renewal.
Mismanaged cloud services put user data at risk

The Research Brief is a short take about interesting academic work.
The big idea
Organizations’ failure to properly manage the servers they lease from cloud service providers can allow attackers to receive private data, research my colleagues and I conducted has shown.
Cloud computing allows businesses to lease servers the same way they lease office space. It’s easier for companies to build and maintain mobile apps and websites when they don’t have to worry about owning and managing servers. But this way of hosting services raises security concerns.
Each cloud server has a unique IP address that allows users to connect and send data. After an organization no longer needs this address, it is given to another customer of the service provider, perhaps one with malicious intent. IP addresses change hands as often as every 30 minutes as organizations change the services they use.
When organizations stop using a cloud server but fail to remove references to the IP address from their systems, users can continue to send data to this address, thinking they are talking to the original service. Because they trust the service that previously used the address, user devices automatically send sensitive information such as GPS location, financial data and browsing history.
An attacker can take advantage of this by “squatting” on the cloud: claiming IP addresses to try to receive traffic intended for other organizations. The rapid turnover of IP addresses leaves little time to identify and correct the issue before attackers start receiving data. Once the attacker controls the address, they can continue to receive data until the organization discovers and corrects the issue. https://www.youtube.com/embed/nHJZHWVgxU8?wmode=transparent&start=0 Poorly managed cloud services are another opportunity for attackers to steal data. Video by Penn State.
Our study of a small fraction of cloud IP addresses found thousands of businesses that were potentially leaking user data, including data from mobile apps and advertising trackers. These apps initially intended to share personal data with businesses and advertisers, but instead leaked data to whoever controlled the IP address. Anyone with a cloud account could collect the same data from vulnerable organizations.
Why it matters
Smartphone users share personal data with businesses through the apps they install. In a recent survey, researchers found that half of smartphone users were comfortable sharing their locations through smartphone apps. But the personal information users share through these apps could be used to steal their identity or hurt their reputation.
Personal data has seen increasing regulation in recent years, and users may be content to trust the businesses they interact with to follow those regulations and respect their privacy. But these regulations may not sufficiently protect users. Our research shows that even when companies intend to use data responsibly, poor security practices can leave that data up for grabs.
Users should know that when they share their private or personal data with companies, they are also exposed to the security practices of those companies. They can take steps to reduce this exposure by reducing how much data they share and with how many organizations they share it.
What other research is being done in this field
Academics and industry are focusing on responsible collection of user data. A recent push by Google aims to reduce collection of users’ personal data by mobile advertisements, ensuring that their security and privacy is protected.
At the same time, researchers are working to better explain what applications do with the data they collect. This work aims to ensure that the data users share with applications is used how they expect by matching permission prompts with how the apps actually behave.
What’s next
We’re conducting research into new technologies on smartphones and devices to ensure they protect user data. For instance, research led by a colleague of mine describes an approach to protect personal data collected by smart cameras. Our vantage point on traffic in the public cloud is also enabling new studies of the internet as a whole. We are continuing to work with cloud providers to ensure that user data stored on the cloud is secure, and are introducing techniques to prevent businesses and their customers from being victimized on the cloud.
Eric Pauley, PhD student in Computer Science and Engineering, Penn State
This article is republished from The Conversation under a Creative Commons license. Read the original article.
Shape-shifting computer chip thwarts an army of hackers

Todd Austin, University of Michigan and Lauren Biernacki, University of Michigan
The Research Brief is a short take about interesting academic work.
The big idea
We have developed and tested a secure new computer processor that thwarts hackers by randomly changing its underlying structure, thus making it virtually impossible to hack.
Last summer, 525 security researchers spent three months trying to hack our Morpheus processor as well as others. All attempts against Morpheus failed. This study was part of a program sponsored by the U.S. Defense Advanced Research Program Agency to design a secure processor that could protect vulnerable software. DARPA released the results on the program to the public for the first time in January 2021.
A processor is the piece of computer hardware that runs software programs. Since a processor underlies all software systems, a secure processor has the potential to protect any software running on it from attack. Our team at the University of Michigan first developed Morpheus, a secure processor that thwarts attacks by turning the computer into a puzzle, in 2019.
A processor has an architecture – x86 for most laptops and ARM for most phones – which is the set of instructions software needs to run on the processor. Processors also have a microarchitecture, or the “guts” that enable the execution of the instruction set, the speed of this execution and how much power it consumes.
Hackers need to be intimately familiar with the details of the microarchitecture to graft their malicious code, or malware, onto vulnerable systems. To stop attacks, Morpheus randomizes these implementation details to turn the system into a puzzle that hackers must solve before conducting security exploits. From one Morpheus machine to another, details like the commands the processor executes or the format of program data change in random ways. Because this happens at the microarchitecture level, software running on the processor is unaffected.

A skilled hacker could reverse-engineer a Morpheus machine in as little as a few hours, if given the chance. To counter this, Morpheus also changes the microarchitecture every few hundred milliseconds. Thus, not only do attackers have to reverse-engineer the microachitecture, but they have to do it very fast. With Morpheus, a hacker is confronted with a computer that has never been seen before and will never be seen again.
Why it matters
To conduct a security exploit, hackers use vulnerabilities in software to get inside a device. Once inside, they graft their malware onto the device. Malware is designed to infect the host device to steal sensitive data or spy on users.
The typical approach to computer security is to fix individual software vulnerabilities to keep hackers out. For these patch-based techniques to succeed, programmers must write perfect software without any bugs. But ask any programmer, and the idea of creating a perfect program is laughable. Bugs are everywhere, and security bugs are the most difficult to find because they don’t impair a program’s normal operation.
Morpheus takes a distinct approach to security by augmenting the underlying processor to prevent attackers from grafting malware onto the device. With this approach, Morpheus protects any vulnerable software that runs on it.
What other research is being done
For the longest time, processor designers considered security a problem for software programmers, since programmers made the software bugs that lead to security concerns. But recently computer designers have discovered that hardware can help protect software.
Academic efforts, such as Capability Hardware Enhanced RISC Instructions at the University of Cambridge, have demonstrated strong protection against memory bugs. Commercial efforts have begun as well, such as Intel’s soon-to-be-released Control-flow Enforcement Technology.
Morpheus takes a notably different approach of ignoring the bugs and instead randomizes its internal implementation to thwart exploitation of bugs. Fortunately, these are complementary techniques, and combining them will likely make systems even more difficult to attack.
What’s next
We are looking at how the fundamental design aspects of Morpheus can be applied to protect sensitive data on people’s devices and in the cloud. In addition to randomizing the implementation details of a system, how can we randomize data in a way that maintains privacy while not being a burden to software programmers?
[Research into coronavirus and other news from science Subscribe to The Conversation’s new science newsletter.]
Todd Austin, Professor of Electrical Engineering and Computer Science, University of Michigan and Lauren Biernacki, Ph.D. Candidate in Computer Science & Engineering, University of Michigan
This article is republished from The Conversation under a Creative Commons license. Read the original article.
How do keys open locks?

Scott Craver, Binghamton University, State University of New York

Curious Kids is a series for children of all ages. If you have a question you’d like an expert to answer, send it to curiouskidsus@theconversation.com.
How are keys made, and how do they open locks? – Noli, age 12, Wisconsin
Have you ever wondered how keys work? I teach a course in computer security where we learn how locks function – and also how they can be broken or bypassed. We do this because locks teach important principles about security in general.
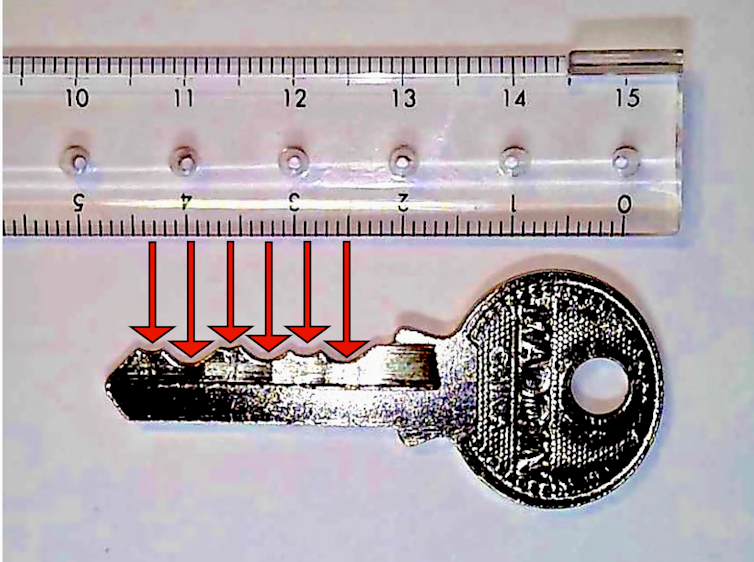
If you look closely at a key, you’ll see its top edge has a bunch of V-shaped valleys. If you inspect the key more closely, perhaps with a ruler, you’ll notice the bottoms of these valleys are equally spaced. The depth of the valleys encodes a sequence that is accepted by the lock, with each valley contributing one value to the combination.
Inside the lock is a cylinder – the part that moves when you stick your key in and turn it. The key can turn only if all its valleys are the right depth for your particular lock.
But how does your lock detect whether your key’s valleys have the right sequence of depths?
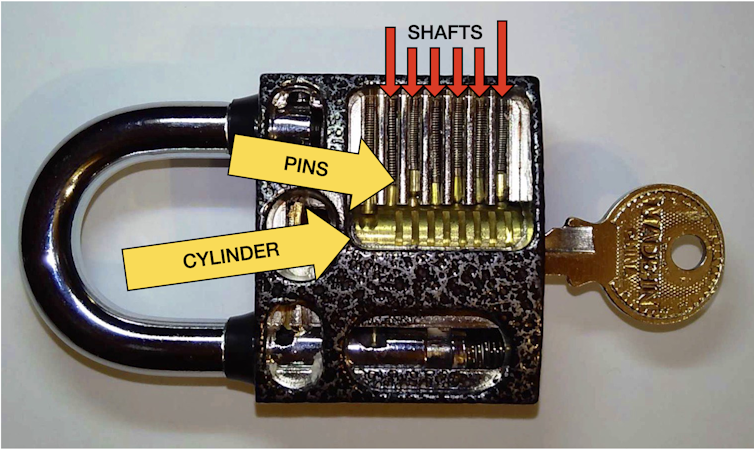
Inside the lock are vertical shafts, one over each valley of the key. In each shaft is a pair of metal pins that can freely slide up and down. Depending on where the pins are, they can block the cylinder from turning and prevent the lock from opening. This happens whenever a pin is partially sticking into or out of the cylinder.

When you stick a key in the lock, the pins fall into the valleys. If a valley is too high, it causes a pin to stick out and jam the cylinder. If a valley is too low, the pin sinks too low and the pin above it will sink into the cylinder and jam it. However, if the right key is inserted with the valleys at just the right depths, none of the pins get in the way.
Keys are made by placing a blank key into a grinding machine that is programmed to carve out the exact valleys that are needed. A locksmith can also change a lock by removing its pins and fitting it with new ones to match a chosen key.
In computer security, we say that security relies on “something you know, something you have or something you are.” A password is an example of something you know. A key is an example of something you have. A fingerprint would be an example of something you are. But as you can see, a key is also very much like a password, except it is encoded by grinding a piece of metal.
For this reason, you shouldn’t ever post a picture of your house key on the internet. That would be like posting a picture of a credit card or a password – someone could use the photo to duplicate the key.
It is also possible to unlock or “pick” locks without a key. By sliding a thin piece of metal into the cylinder and gently pushing the pins to the correct height one by one, locks can be opened. However, it takes a great deal of skill and practice to do this.
What does this teach us about security? First, we must make keys secret by making a very large number of possible keys, so that the right one is hard to guess or build. It’s the same for passwords. Second, it’s important to engineer a lock or computer program that requires every bit of the key or password to be exactly correct.
It’s important to study the inner workings of locks and computer programs to understand how their design might allow someone to break them.
Hello, curious kids! Do you have a question you’d like an expert to answer? Ask an adult to send your question to CuriousKidsUS@theconversation.com. Please tell us your name, age and the city where you live.
And since curiosity has no age limit – adults, let us know what you’re wondering, too. We won’t be able to answer every question, but we will do our best.
Scott Craver, Associate Professor of Electrical and Computer Engineering, Binghamton University, State University of New York
This article is republished from The Conversation under a Creative Commons license. Read the original article.
Unbreakable by Pokki DJ (Youtube Video)
Excellent Artist, I found on Jamendo, you can find him on Itunes, AMazon and a few other music sites for purchace / Download.
Better by Square a Saw
The River by Stingray Szn











